if ($request_uri ~* "([+|(%20)]and[+|(%20)])|([+|(%20)]or[+|(%20)])|([+|(%20)]select[+|(%20)])|([+|(%20)]exec[+|(%20)])|([+|(%20)]union[+|(%20)])") {return 404;}if ($request_uri ~* "(cost\()|(concat\()") {return 404;}if ($query_string ~ "(<|%3C).*script.*(>|%3E)") {return 404;}if ($query_string ~ "GLOBALS(=|[|%[0-9A-Z]{0,2})") {return 404;}if ($query_string ~ "_REQUEST(=|[|%[0-9A-Z]{0,2})") {return 404;}if ($query_string ~ "proc/self/environ") {return 404;}if ($query_string ~ "mosConfig_[a-zA-Z_]{1,21}(=|%3D)") {return 404;}if ($query_string ~ "base64_(en|de)code(.*)") {return 404;}if ($http_user_agent ~ "Python-urllib") {return 404;}转载请注明:IT运维空间 » linux » 利用nginx重写规则防止SQL注入攻击通用规则
继续浏览有关 LINUX技术 的文章

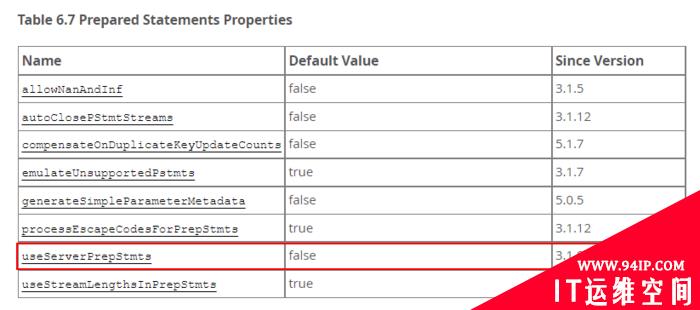







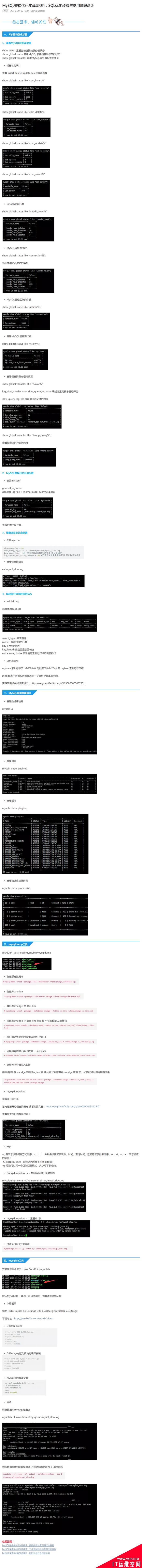

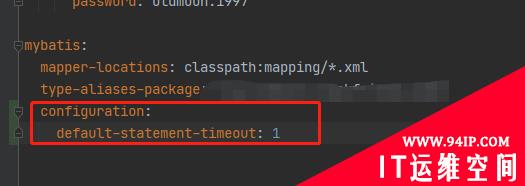
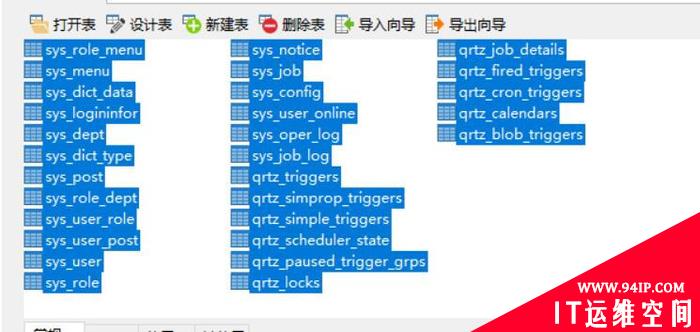






发表评论