在前面篇中,我们介绍了基于PSK的IPsec VPN配置的相关信息,接下来,我们继续讲解关于采用积极模式并PSK的IPsec VPN配置的内容。
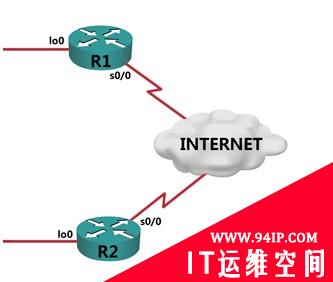
1.R1基本配置:
R1(config)#interfaceloopback0 R1(config-if)#ipaddress10.1.1.1255.255.255.0 R1(config-if)#noshutdown R1(config-if)#interfaceserial0/0 R1(config-if)#ipaddress192.168.1.1255.255.255.252 R1(config-if)#clockrate56000 R1(config-if)#noshutdown R1(config-if)#exit
2.定义感兴趣流量与路由协议:
R1(config)#access-list100permitip10.1.1.00.0.0.25510.2.2.00.0.0.255 R1(config)#iproute0.0.0.00.0.0.0serial0/0
3.全局启用ISAKMP并定义对等体及其PSK(预共享密钥),采用积极模式:
R1(config)#cryptoisakmpenable R1(config)#cryptoisakmppeeraddress192.168.1.2 R1(config-isakmp-peer)#setaggressive-modeclient-endpointipv4-address192.168.1.1 R1(config-isakmp-peer)#setaggressive-modepassword91lab
4.定义IKE策略:
R1(config)#cryptoisakmppolicy10 R1(config-isakmp)#encryptionaes128/---默认是DES加密---/ R1(config-isakmp)#hashsha/---默认是SHA-1---/ R1(config-isakmp)#authenticationpre-share R1(config-isakmp)#group2/---默认是768位的DH1---/ R1(config-isakmp)#lifetime3600/---默认是86400秒---/ R1(config-isakmp)#exit
5.定义IPSec转换集(transform set):
R1(config)#cryptoipsectransform-setttesp-aes128esp-sha-hmac R1(cfg-crypto-trans)#modetunnel R1(cfg-crypto-trans)#exit
6.定义crypto map并应用在接口上:
R1(config)#cryptomapcisco10ipsec-isakmp R1(config-crypto-map)#matchaddress100 R1(config-crypto-map)#setpeer192.168.1.2/---定义要应用cryptomap的对等体地址---/ R1(config-crypto-map)#settransform-settt/---定义cryptomap要应用的IPsec转换集---/ R1(config-crypto-map)#exit R1(config)#interfaceserial0/0 R1(config-if)#cryptomapcisco *Mar100:08:31.131:%CRYPTO-6-ISAKMP_ON_OFF:ISAKMPisON R1(config-if)#end R1#
R1配置完成.
同理,R2配置如下:
! ! cryptoisakmppolicy10 encraes authenticationpre-share group2 ! cryptoisakmppeeraddress192.168.1.1 setaggressive-modepassword91lab setaggressive-modeclient-endpointipv4-address192.168.1.1 ! ! cryptoipsectransform-setttesp-aesesp-sha-hmac ! cryptomapcisco10ipsec-isakmp setpeer192.168.1.1 settransform-settt matchaddress100 ! ! ! ! interfaceLoopback0 ipaddress10.2.2.1255.255.255.0 ! interfaceSerial0/0 ipaddress192.168.1.2255.255.255.252 cryptomapcisco ! iproute0.0.0.00.0.0.0Serial0/0 ! access-list100permitip10.2.2.00.0.0.25510.1.1.00.0.0.255 !
转载请注明:IT运维空间 » 安全防护 » 采用积极模式并PSK的IPsec VPN配置














发表评论