
Docker scan[1]本地扫描镜像漏洞
2020年年底,Docker hub推出镜像自动扫描的功能,同时Docker也支持了在本地通过Docker命令选项的方式支持镜像漏洞扫描,目前Docker Desktop for Mac以及window上的Docker都可以通过Docker scan子命令扫描本地镜像是否存在漏洞软件。
Docker Desktop For Mac
使用docker scan的时候需要登录Docker Hub的账号,同时docker scan支持一些不同的选项
Options: --accept-license接受使用第三方扫描提供商 --dependency-tree显示带有扫描结果的依赖树 --exclude-base从漏洞扫描中排除基础镜像(requires--file) -f,--filestring与image关联的Dockerfile,提供更详细的结果 --group-issues聚合重复的漏洞并将其分组为1个漏洞(requires--json) --json以json格式输出结果 --login使用可选令牌(带有--token)向扫描提供程序进行身份验证,如果为空则使用webbase令牌 --reject-license拒绝使用第三方扫描提供商 --severitystring只报告提供级别或更高的漏洞(low|medium|high) --tokenstring登录到第三方扫描提供程序的认证令牌 --version显示扫描插件版本
指定Dockerfile
$dockerscan-fDockerfiledocker-scan:e2e Testingdocker-scan:e2e ... ✗Highseverityvulnerabilityfoundinperl Description:IntegerOverfloworWraparound Info:https://snyk.io/vuln/SNYK-DEBIAN10-PERL-570802 Introducedthrough:git@1:2.20.1-2+deb10u3,meta-common-packages@meta From:git@1:2.20.1-2+deb10u3>perl@5.28.1-6 From:git@1:2.20.1-2+deb10u3>liberror-perl@0.17027-2>perl@5.28.1-6 From:git@1:2.20.1-2+deb10u3>perl@5.28.1-6>perl/perl-modules-5.28@5.28.1-6 and3more... Introducedbyyourbaseimage(golang:1.14.6) Organization:docker-desktop-test Packagemanager:deb Targetfile:Dockerfile Projectname:docker-image|99138c65ebc7 Dockerimage:99138c65ebc7 Baseimage:golang:1.14.6 Licenses:enabled Tested200dependenciesforknownissues,found157issues. Accordingtoourscan,youarecurrentlyusingthemostsecureversionoftheselectedbaseimage
不扫描该镜像的基础镜像
$dockerscan-fDockerfile--exclude-basedocker-scan:e2e Testingdocker-scan:e2e ... ✗Mediumseverityvulnerabilityfoundinlibidn2/libidn2-0 Description:ImproperInputValidation Info:https://snyk.io/vuln/SNYK-DEBIAN10-LIBIDN2-474100 Introducedthrough:iputils/iputils-ping@3:20180629-2+deb10u1,wget@1.20.1-1.1,curl@7.64.0-4+deb10u1,git@1:2.20.1-2+deb10u3 From:iputils/iputils-ping@3:20180629-2+deb10u1>libidn2/libidn2-0@2.0.5-1+deb10u1 From:wget@1.20.1-1.1>libidn2/libidn2-0@2.0.5-1+deb10u1 From:curl@7.64.0-4+deb10u1>curl/libcurl4@7.64.0-4+deb10u1>libidn2/libidn2-0@2.0.5-1+deb10u1 and3more... IntroducedinyourDockerfileby'RUNapkadd-U--no-cachewgettar' Organization:docker-desktop-test Packagemanager:deb Targetfile:Dockerfile Projectname:docker-image|99138c65ebc7 Dockerimage:99138c65ebc7 Baseimage:golang:1.14.6 Licenses:enabled Tested200dependenciesforknownissues,found16issues.
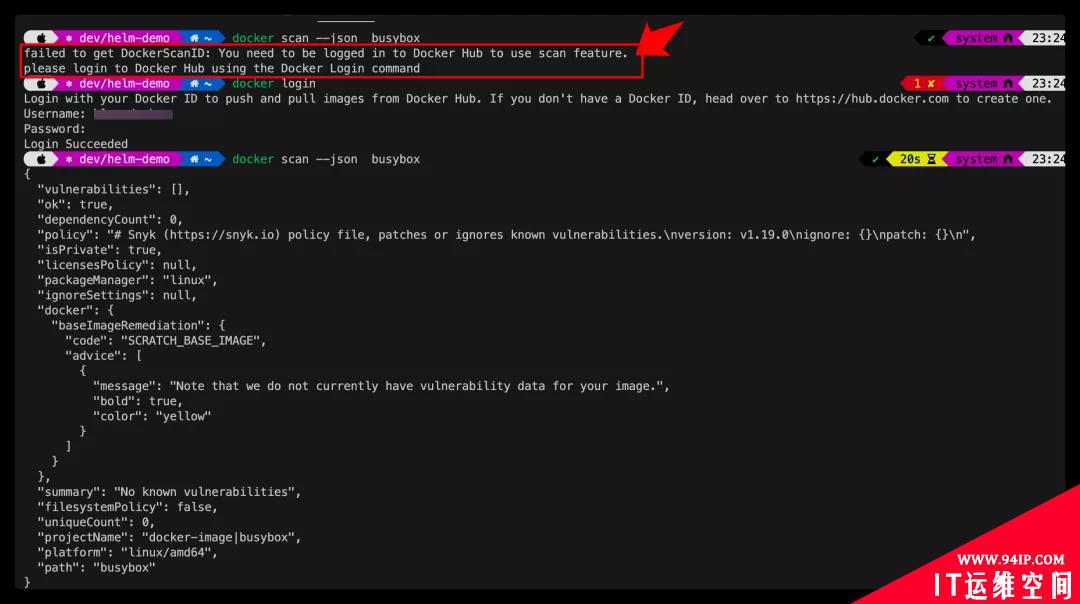
以json格式输出扫描结果
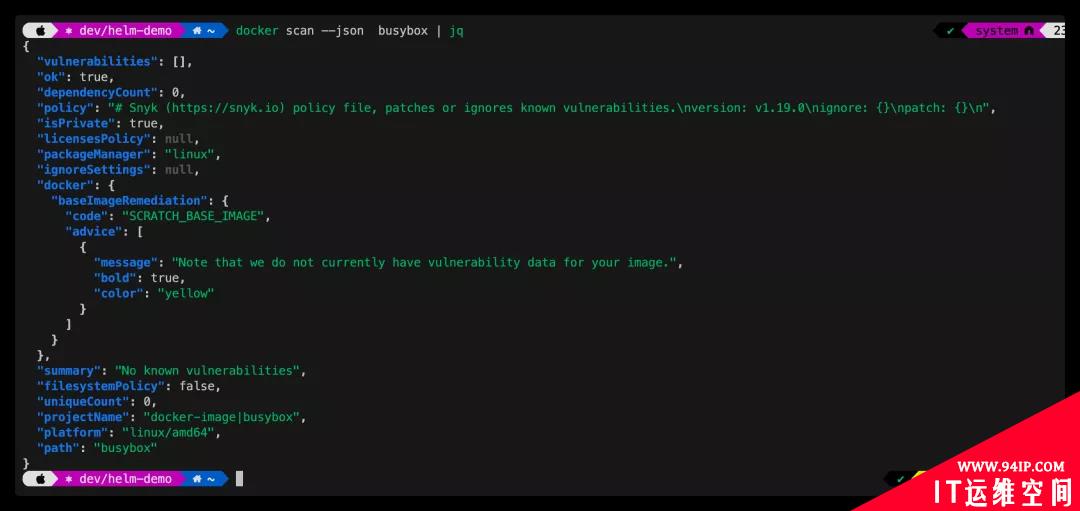
JSON格式显示镜像扫描结果
聚合分组显示扫描信息
$dockerscan--json--group-issuesdocker-scan:e2e
{
{
"title":"ImproperCheckforDroppedPrivileges",
...
"packageName":"bash",
"language":"linux",
"packageManager":"debian:10",
"description":"##Overview\nAnissuewasdiscoveredindisable_priv_modeinshell.cinGNUBashthrough5.0patch11.Bydefault,ifBashisrunwithitseffectiveUIDnotequaltoitsrealUID,itwilldropprivilegesbysettingitseffectiveUIDtoitsrealUID.However,itdoessoincorrectly.OnLinuxandothersystemsthatsupport\"savedUID\"functionality,thesavedUIDisnotdropped.Anattackerwithcommandexecutionintheshellcanuse\"enable-f\"forruntimeloadingofanewbuiltin,whichcanbeasharedobjectthatcallssetuid()andthereforeregainsprivileges.However,binariesrunningwithaneffectiveUIDof0areunaffected.\n\n##References\n-[CONFIRM](https://security.netapp.com/advisory/ntap-20200430-0003/)\n-[DebianSecurityTracker](https://security-tracker.debian.org/tracker/CVE-2019-18276)\n-[GitHubCommit](https://github.com/bminor/bash/commit/951bdaad7a18cc0dc1036bba86b18b90874d39ff)\n-[MISC](http://packetstormsecurity.com/files/155498/Bash-5.0-Patch-11-Privilege-Escalation.html)\n-[MISC](https://www.youtube.com/watch?v=-wGtxJ8opa8)\n-[UbuntuCVETracker](http://people.ubuntu.com/~ubuntu-security/cve/CVE-2019-18276)\n",
"identifiers":{
"ALTERNATIVE":[],
"CVE":[
"CVE-2019-18276"
],
"CWE":[
"CWE-273"
]
},
"severity":"low",
"severityWithCritical":"low",
"cvssScore":7.8,
"CVSSv3":"CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:F",
...
"from":[
"docker-image|docker-scan@e2e",
"bash@5.0-4"
],
"upgradePath":[],
"isUpgradable":false,
"isPatchable":false,
"name":"bash",
"version":"5.0-4"
},
...
"summary":"880vulnerabledependencypaths",
"filesystemPolicy":false,
"filtered":{
"ignore":[],
"patch":[]
},
"uniqueCount":158,
"projectName":"docker-image|docker-scan",
"platform":"linux/amd64",
"path":"docker-scan:e2e"
}
显示指定级别的漏洞,只有高于此级别的漏洞才会显示出来
$dockerscan--severity=mediumdocker-scan:e2e ./bin/docker-scan_darwin_amd64scan--severity=mediumdocker-scan:e2e Testingdocker-scan:e2e... ✗Mediumseverityvulnerabilityfoundinsqlite3/libsqlite3-0 Description:DivideByZero Info:https://snyk.io/vuln/SNYK-DEBIAN10-SQLITE3-466337 Introducedthrough:gnupg2/gnupg@2.2.12-1+deb10u1,subversion@1.10.4-1+deb10u1,mercurial@4.8.2-1+deb10u1 From:gnupg2/gnupg@2.2.12-1+deb10u1>gnupg2/gpg@2.2.12-1+deb10u1>sqlite3/libsqlite3-0@3.27.2-3 From:subversion@1.10.4-1+deb10u1>subversion/libsvn1@1.10.4-1+deb10u1>sqlite3/libsqlite3-0@3.27.2-3 From:mercurial@4.8.2-1+deb10u1>python-defaults/python@2.7.16-1>python2.7@2.7.16-2+deb10u1>python2.7/libpython2.7-stdlib@2.7.16-2+deb10u1>sqlite3/libsqlite3-0@3.27.2-3 ✗Mediumseverityvulnerabilityfoundinsqlite3/libsqlite3-0 Description:UncontrolledRecursion ... ✗Highseverityvulnerabilityfoundinbinutils/binutils-common Description:MissingReleaseofResourceafterEffectiveLifetime Info:https://snyk.io/vuln/SNYK-DEBIAN10-BINUTILS-403318 Introducedthrough:gcc-defaults/g++@4:8.3.0-1 From:gcc-defaults/g++@4:8.3.0-1>gcc-defaults/gcc@4:8.3.0-1>gcc-8@8.3.0-6>binutils@2.31.1-16>binutils/binutils-common@2.31.1-16 From:gcc-defaults/g++@4:8.3.0-1>gcc-defaults/gcc@4:8.3.0-1>gcc-8@8.3.0-6>binutils@2.31.1-16>binutils/libbinutils@2.31.1-16>binutils/binutils-common@2.31.1-16 From:gcc-defaults/g++@4:8.3.0-1>gcc-defaults/gcc@4:8.3.0-1>gcc-8@8.3.0-6>binutils@2.31.1-16>binutils/binutils-x86-64-linux-gnu@2.31.1-16>binutils/binutils-common@2.31.1-16 and4more... Organization:docker-desktop-test Packagemanager:deb Projectname:docker-image|docker-scan Dockerimage:docker-scan:e2e Platform:linux/amd64 Licenses:enabled Tested200dependenciesforknownissues,found37issues.
Linux上安装scan-cli插件
目前Linux系统上的Docker Engine尚未支持scan命令,因此可以通过插件形式使用,可以参考scan-cli-plugin[2]的文档,此处我在Ubuntu上通过apt安装一下
>cat/etc/apt/sources.list.d/docker.list deb[arch=amd64]https://mirrors.aliyun.com/docker-ce/linux/ubuntuxenialstable >apt-getupdate&&apt-getinstalldocker-scan-plugin
安装完成之后,登录Docker hub,然后同意访问Snyk即可。
参考资料
[1]docker scan:
https://docs.docker.com/engine/scan/
[2]scan-cli-plugin:
https://github.com/docker/scan-cli-plugin
转载请注明:IT运维空间 » 安全防护 » "docker scan"本地扫描镜像漏洞









发表评论